Securing a web application is crucial these days. When it comes to web developers, fixing the vulnerabilities should start from the first floor; from the developer himself. You, as a simple developer, do not really need to know all the hustle and bustle of pen testing. There are several good tools for scanning web applications. I will show you one of the easiest ways to run a web penetration with the tool OWASP ZAP (Zed Attack Proxy).
What is OWASP ZAP?
OWASP (Open Web Application Security Project) is worldwide non-profit organization focused on improving the security of software.

OWASP ZAP (Zed Attack Proxy) is one of the world’s most popular security tools. It’s a part of the OWASP community, which means it’s totally free.
Why did I choose OWASP ZAP?
It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing.
ZAP is cross-platform. What it does is create a proxy between the client and your website. While you navigate through all the features of your website, it captures all actions. Then, it attacks your website with the known techniques. The good part is;
Yeap, it’s open-source!
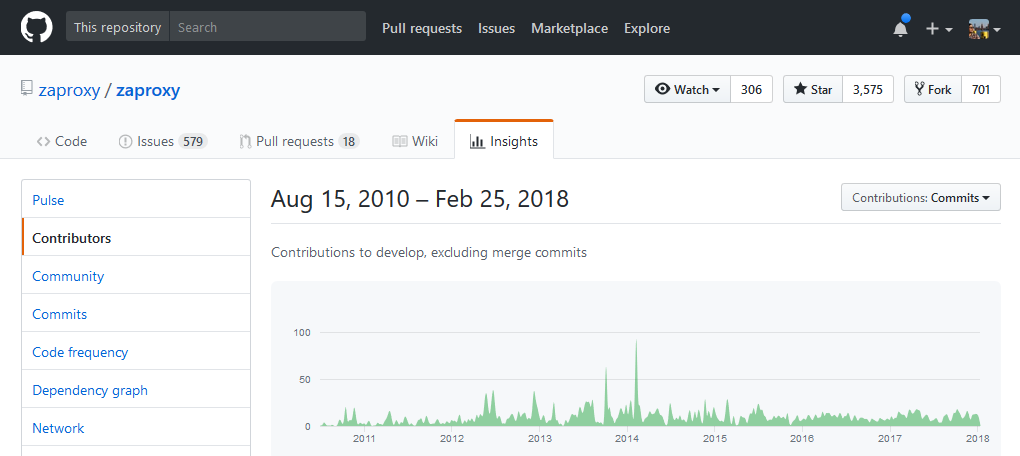
At the time I visited their repository, the last commit was 40 minutes ago. It’s a very active repository. The project was initiated in 2010 and is still being improved. See the GitHub repository https://github.com/zaproxy/zaproxy.
Setting up your ZAP Environment
- JAVA 8+ : In order to install ZAP, you need to install JAVA 8+ to your Windows or Linux system. If you use the Mac OS, you don’t need JAVA as it’s already installed. Go to [https://java.com/en/download/](http













mobilemechanicforlv 4 years ago
Hi! Your article “OWASP ZAP” is very helpful for me. After reading your article I got a lot of knowledge about owasp ZAP.I am trying to get some information about auto mechanic from this article.
clifford.ssmithh@gmail.com 4 years ago
This is really informative. Thanks for sharing this blog as it helps web testing enthusiasts like me. Have you published a blog on web testing tools? I have used tools like QARA Enterprise and Katalon Studio.
Enriquluise 5 years ago
All the time, it won't work. For example, if a project goes through maintenance and an unexpected problem arises and if the team is accused of failing through test the scenario and if the documentation does not cover it, then how are we going to prove that it is covered during testing? Last year, with the first POCO branded smartphone, Xiaomi launched its POCO sub-brand on 22 August. In particular, the Pocophone F1, which is used when playing sports. More info: https://mobilearrival.com/xiaomi-ninebot-unveils-e-bikes-with-smart-features/